The Bitcoin blockchain is rightfully considered the safest and most reliable decentralized system, where integrity is achieved through cryptography. The emergence of Bitcoin made it possible to solve the so-called double-spending problem.
However, since the Bitcoin network and blockchain technology are still young, there are a number of vulnerabilities that can disrupt the functioning of the network and lead to the double-spending of funds and even more severe consequences.
In this article, we will review the most prevalent real and hypothetical attacks on cryptocurrency networks.
Dangerous attacks include:
1) 51% attack
2) Selfish mining
3) Sybil attack
4) Finney attack
5) A single-confirmation attack

51% Attack
Anyone somewhat familiar with the crypto space has heard that such an attack could destroy the entire network. Back in October 2008, Satoshi Nakamoto’s Bitcoin white paper pointed out the possibility of such events in the Bitcoin network. Satoshi described why it would be disadvantageous for the attacker himself. Yet, over the entire existence of cryptocurrencies, there have been cases of successful attacks taking advantage of this vulnerability. This represents a high level of threat, and the scale of the ramifications of such an event would be extremely harmful to the leading cryptocurrency.
The functioning of the Bitcoin network and many other blockchains is based on PoW (Proof of Work) and is supported by miners. Miners use their devices ’computing power to secure the network, receiving a reward in the form of newly created coins. Moreover, mining is the only way to increase the number of coins in circulation.
Mining as a process is intended to create network blocks that would record all the transactional information. The created blocks are built in a linear manner and form a blockchain.
For a miner to add a new block, they need to make calculations of a certain complexity in order to prove the completion of their work. But since there is more than one miner on the network, each miner competes to do it faster than the others. The more computing power a miner has, the higher their chance of adding a block to the chain and receiving a reward.
In case a single miner manages to control more than 50% of the network’s computing resources, they will be able to gain control over the entire network. In this case, they will get the opportunity to:
- create blocks;
- stop adding information about transactions;
- revert transactions;
- exercise double-spending;
- split blockchains.
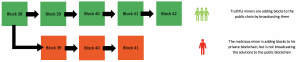
History has shown cases of successful 51% attacks on other blockchains built on the PoW algorithm. In 2018 alone, between May and June, six attacks on such cryptocurrencies as Horizen (ZEN), Litecoin Cash (LCC), Bitcoin Gold (BTG), Monacoin (MONA) and also two attacks on Verge (XVG)
Selfish mining
To understand such an attack, we need to take a closer look at how the blockchain is formed.
In the process of mining, a situation may occur where one block may precede two new blocks. However, as we know, blockchain is meant to be a sequential chain of blocks. Therefore, in case of a split of the chain into two parallel ones, both branches will be equally meaningful until one of them becomes longer (the one where the last block appears faster).
Based on this rule, in order for the chain to be taken as the correct one, it simply needs to become longer than its competing chain. To receive a reward for finding a block, the miner must distribute the mined block across the network faster than the others. Otherwise, the competing chain may be accepted as the correct one.
Selfish mining implies actions during which the attacker earns more than others for a certain period of time without distributing his block over the network. Such a network attack is a variation of a double-spending attack.
Sybil attack
This attack was named after a clinical psychology case related to the treatment of dissociative identity disorder. Theoretically, such an attack is most likely to occur in peer-to-peer networks, not limited to just Bitcoin.
Bitcoin is a network of connected nodes. The possibility of an attack is based on the fact that it is impossible to reliably distinguish nodes in the network. Therefore, an attacker tries to take control of neighboring nodes or launch their own node, spreading false information. Having gained control over the nodes, the attacker can:
- block transactions from other users by disconnecting the node from the shared network;
- identify transactions of the captured node;
- transmit false data.
In the Bitcoin network, nodes are connected randomly, so it is impossible to determine which nodes would be connected. Countering this attack is embedded in the Bitcoin software architecture. To find a block and get coins, the node needs to spend as many resources as possible. Therefore, it is costly to control a large number of nodes.
Outside of cryptocurrency space, such an attack was carried out on the Tor network in 2014.
Finney attack
The possibility of such an attack was first assumed by Hal Finney, Bitcoin developer, and the first recipient of a 10 BTC transaction from Satoshi Nakamoto. The attack has several varieties.
The attacker, completing the mining process, finds the blocks and adds certain transactions, sending their funds to new addresses they own. In this case, the blocks are not broadcasted to the network but form a secret chain. Then they send the same funds to a merchant, repeatedly spending the funds. The merchant receives the funds, transfers the goods, and the attacker broadcasts their block, containing the transaction, which sends their own funds to one of the new addresses created previously, provided that this transaction is accepted earlier.
The greater the attacker’s computing power, the higher the likelihood of success for such an attack.
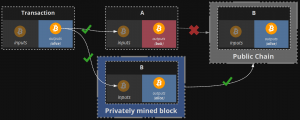
Accepting or sending payments with zero confirmations is not advisable and can lead to a loss of funds, precisely because of the possibility of this type of attack. You must wait for at least two network confirmations to ensure the safety of the funds. But even with two confirmations, the probability of Finney attacks may be quite high.
Single confirmation attack
This is another type of double-spending described on the bitcointalk forum by the user under the nickname Vector76. It combines both the Finney attack and the Race attack.
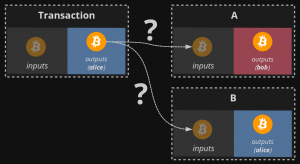
The principle of the Vector76 attack is to sacrifice the mined block and send it to the victim’s node instead of broadcasting it to the network. Important conditions for the attack are a maximum of one transaction confirmation and the host’s permission to accept incoming connections.
At the moment, it is quite difficult to fulfill both of these conditions, since all popular wallets and major exchanges abide by the rules of a large number of transaction confirmations.
Conclusion
Bitcoin’s blockchain is the most secure one in the industry, as it was the first of its kind and gave an impetus to the development of the crypto industry. The significant computing power involved in the mining process guarantees network security. A huge amount of resources would be required to carry out at least one of the attacks described in the article; this casts doubt on their implementation’s economic feasibility.
But this does not mean that each user of the network is safe. There are numerous other ways to take over the funds. Blockchains, which are the base for the other cryptocurrencies, can be susceptible to different types of attacks. Therefore, in order to use cryptocurrencies and stay confident regarding the security of your funds, it is vital to understand the basics of these instruments.


