Building decentralized financial institutions and an independent financial system is a truly revolutionary idea. Blockchain, smart contracts and the ability to create dApps allow each of its participants to have full control over their funds. Decentralized finance is designed to provide access to financial services and operations, such as: lending, loans, provision of liquidity, trading, release of assets, and also allows you to build trust without the need for trust as such.

As soon as it comes to finances, do not forget about the confidentiality of your personal data and your funds. In this article, we’ll talk about the solutions that are being developed to help improve the privacy of your transactions and transactions in the DeFi ecosystem..
About privacy issues
Since the history of all transactions in the blockchain is stored in the public domain, any outside observer can analyze it and use it to de-anonymize participants, together with other collected data received about them..
Members interact with the DeFi ecosystem through smart contracts. Due to the transparency of all data stored on the blockchain, it is impossible to store confidential data inside smart contracts. And therefore, data on the amounts and conditions of the contract are visible to everyone..
Blockchain technology is based on principles that provide a fairly high level of anonymization, which is why more and more companies in need of a high level of confidentiality are exploring the possibilities of distributed systems..
DeFi’s privacy means that it is not possible to obtain data that can be used to identify the owner of the wallet. Below we look at examples of projects and solutions that work to improve the privacy of DeFi members..
Confidential smart contracts
In February 2019, a group of scientists from Stanford University created a mechanism for securing private smart contracts on the Ethereum network – Zether. The Zether mechanism allows you to create new types of smart contracts, where account balances are encrypted and stored until the moment the deposit is made, and the funds are closed in the contract and remain locked there..
Using the Zether mechanism, users send ETH to the ZSC contract, and in return receive an equivalent amount in ZTH tokens, which are used for hidden transactions. Also, Zether implemented the ability to hide information about the participants in the transaction at the decision of the initiator of the transaction..
Touching upon smart contracts and ensuring privacy, it is worth mentioning the Enigma project, which develops solutions for creating secret smart contracts focused on the security of user data..
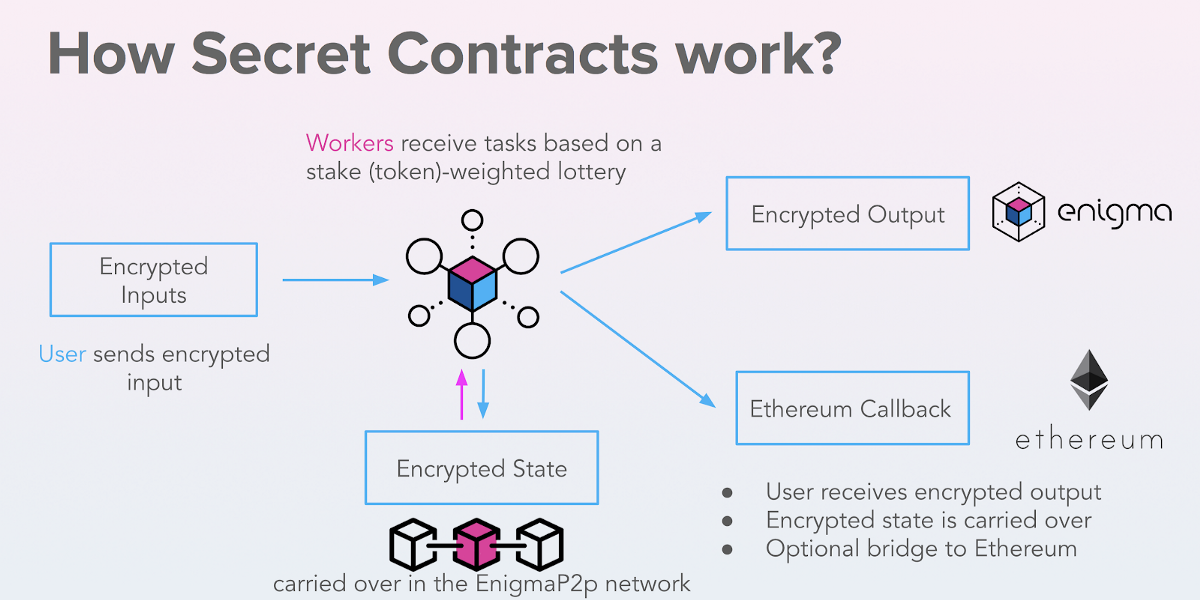
Enigma secret contracts, which store blockchain data in encrypted form, can interact with each other. Operating outside of the Ethereum network, contract data is fragmented, encrypted, and distributed among the network nodes. When requesting data, nodes provide it without publicly disclosing the information. To ensure data privacy, the Zero-knowledge proof algorithm is used, a modification of which is used in the Zcash cryptocurrency.
Ensuring the security and privacy of the user using smart contracts is especially important, for example, during lending operations, auctions or any financial transactions. At the moment, these projects are mainly research activities and have only the potential to be useful in ensuring the privacy of the user and his funds..
Mixing technology
One way to ensure privacy is by using coin mixing services. During the mixing process, funds from several users are mixed with each other and then reach their destination. It is almost impossible to trace who owns certain products after mixing. One of the most popular solutions in this direction is the ETH mixing service – Tornado Cash, which allows you to mix transactions using Zero-knowledge proofs and encryption of user funds..
The updated version of the service has the ability to mix ERC-20 tokens – DAI.
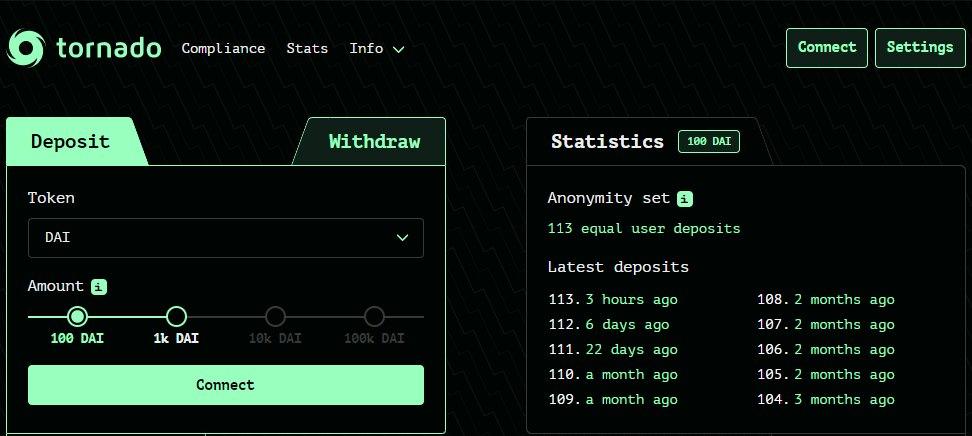
Service management through a smart contract allows Tornado Cash to remain truly decentralized since no centralized trusted party takes over the storage or control of funds during the mixing process.
In May 2020, the developers of Tornado Cash restricted access to changing the smart contract code, which, on the one hand, indicates the absence of a centralized management body, and on the other hand, attracts attackers to try to hack the managing smart contract..
DeFi Privacy Solutions
One of the biggest problems with decentralized finance is the fact that most of its applications are not private. Transactions built on the Ethereum blockchain are publicly available to all network participants. The developers of the privacy-oriented cryptocurrency Beam held a hard fork in July 2020, where they activated the so-called Confidential Assets (CA – Confidential Assets).
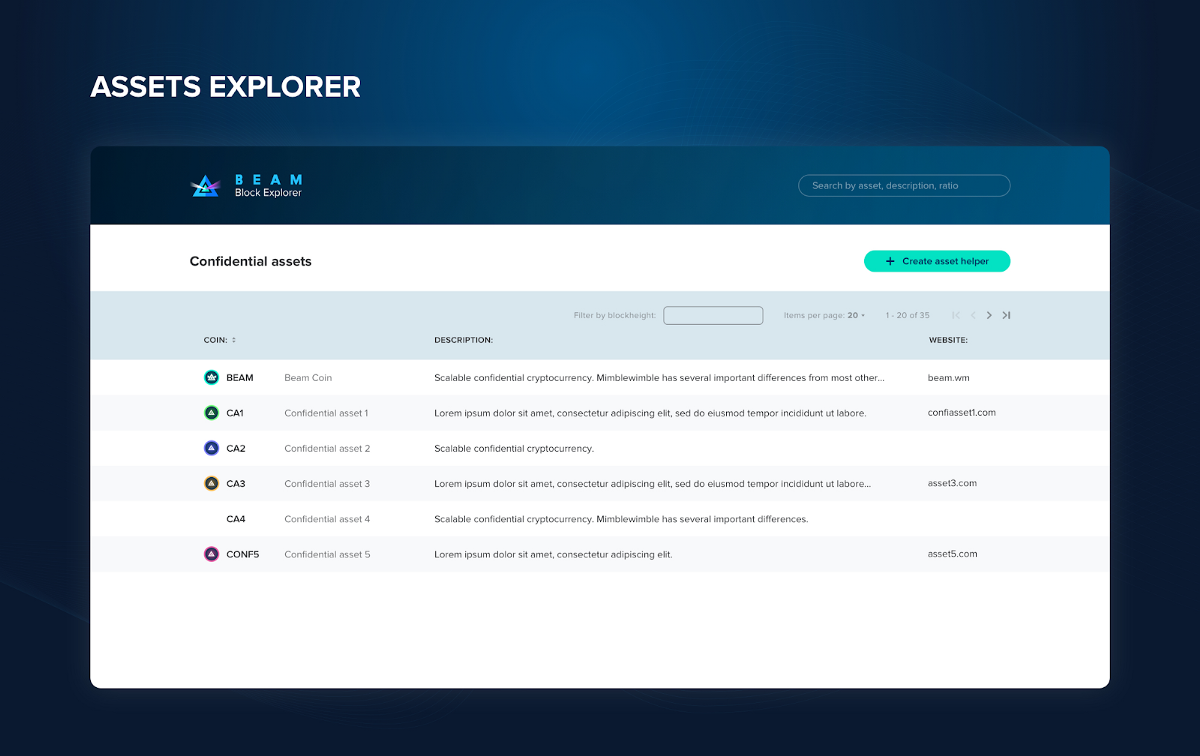
Developers want to build a DeFi ecosystem within the Beam network, where CAs will be Beam-independent private DeFi tokens designed to create dApps. In the hard fork, together with CA, functions were also added for creating “scriptless contracts” – unwritten contracts where contract details and transactions themselves remain confidential, as well as full support for “atomic swap” on Beam DEX.
Another project focused on privacy in DeFi is Incognito, whose developers intend to ensure the privacy of tokens of other blockchains. Incognito’s privacy technology is based on the same principles as Monero. The project focuses on interoperability with other blockchains, offering support for lending and anonymous deposits, in “shielded” ETH (pETH), which are backed by real ETH. \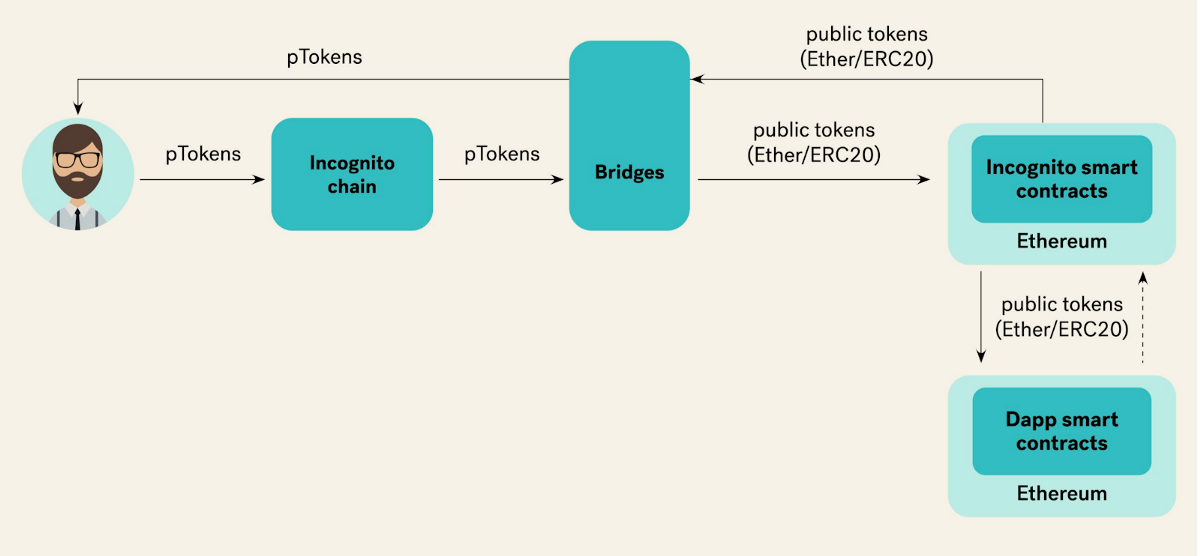
Incognito is planning to launch private versions of DeFi platforms that do not support full-fledged smart contracts, but allow the creation of tokens according to certain scenarios, which allows building bridges with other smart contract platforms. So, in early July, the platform was released pKyber, which interacts with DEX Kyber through Incognito.
Another project is developing and building bridges between blockchains – NIX Bridge. It is a privacy protocol that ensures the privacy of any ERC20 token on the NIX network..
Conclusion
All of the above solutions and projects are meaningless if users do not follow the basic rules for ensuring their information security and the security of their data. If you do not hide your own IP address in order to conduct your activities on the DeFi system, your location information may be correlated with your accounts and transaction history. For this reason, in order to maintain your privacy, you need to take measures to hide your IP address, for example, use a VPN or TOR.
With the advent of DeFi, Ethereum’s popularity has skyrocketed with new dApps on the platform. In the DeFi ecosystem, to date, $ 11 billion is blocked, which indicates an increased demand for both financial instruments and the data of users who use these instruments. The development of solutions to improve the privacy and security of user data is gaining momentum, which will have a positive impact on the future of decentralized finance.


